|
When considering how easy it might be for you to break into encryption secheme, one can distinguish three
different scenarios, depending on what information the intruder has.
- Ciphertext-only attack. We have seen how statistical analysis can help in a ciphertext-only
attack on an encryption scheme.
- Known-plaintext attack. When an intruder knows some of the pairing, we refer to this as a
known-plaintext attack on the encryption scheme.
- Chosen-plaintext attack. In a chosen-plaintext attack, the intruder is able
to choose the plaintext message and obtain its corresponding ciphertext form.
Five hundred years ago, techniques improving on nonoalphabetic encryption known as polyalphabetic encryption,
were invented. The idea behind polyalphabetic encryption is to use multiple monoalphbetic ciphers, with a specific monoalphabetic
cipher to encode a letter in a specific position in the plaintext message.
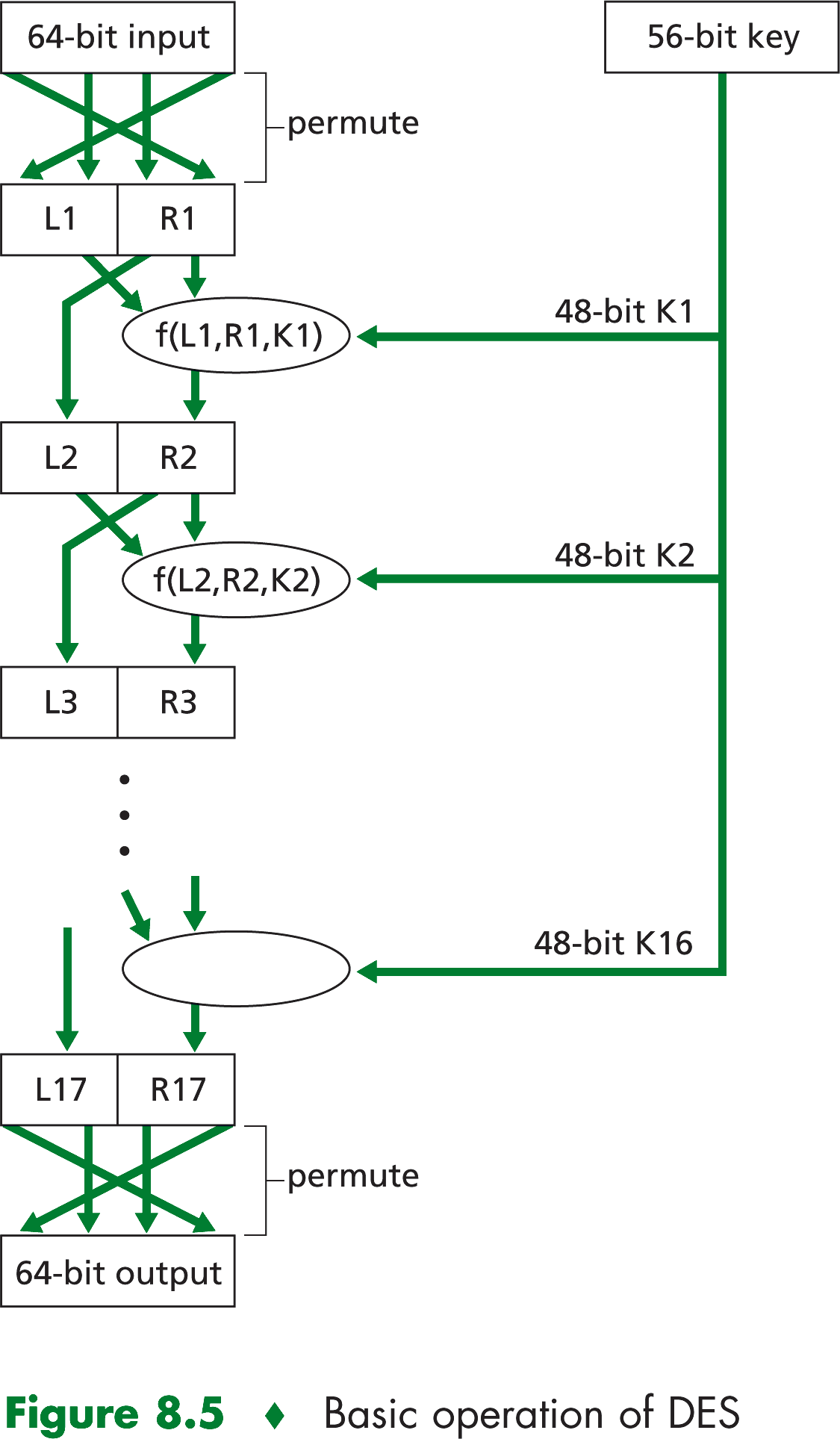
Data Encryption Standard (DES) and Advanced Encryption Standard (AES)
A symmetric key encryption standard published in 1977 and updated most recently in 1993 by the US National
Bureau of Standards for commercial and nonclassified US government use. DES encodes plaintext in 64-bit chuncks using
a 64-bit key. Actually, 8 of these 64 bits of the key are odd parity bits , so the DES key is effectively 56 bits
long. The National Institute of Standards and Technology states the goal of DES as follows: "The goal is to completely
scramble the data and key so that every bit of the ciphertext depends on every bit of the data and every bit of the key....With
a good algorithm, there should be no correlation between the ciphertext and either the original data or key".

In 1997, a network security company, RSA Data Security Inc., launched a DES Challenge contest to crack (decode)
a short phrase it had encrypted unsing 56-bit DES. The unencodeed phrase ("Strong cryptography makes the world a safer
place.) was determined in less than four months by a team that used volunteers throughout the Internet to systematically explore
the key space.
NIST announced the successor to DES: the Advanced Encryption Stnadard (AES), also known as the Rijndata
in 128-bit blocks and can operate with key algorithm that processes NIST estimates that a machine that could crack 50-bit
DES in one second would take approminately 149 trillion years to crack a 128-bit AES key.
|
