|
The use of a nonce and symmetric key cryptograhpy formed the basis of our successful authentication protocol, ap4.0.
A natural question is whether we can use a nonce and public key cryptography to solve the authentication problem. The use
of a public key approach would obviated a difficulty in any shared bey system--worrying about how the two parties learn the
secret shared key value in the first place. A protocol that uses public key cryptograhpy in a manner analogous to the
use of symmetric key cryptographty in protocol ap4.0 is protocol ap5.0.
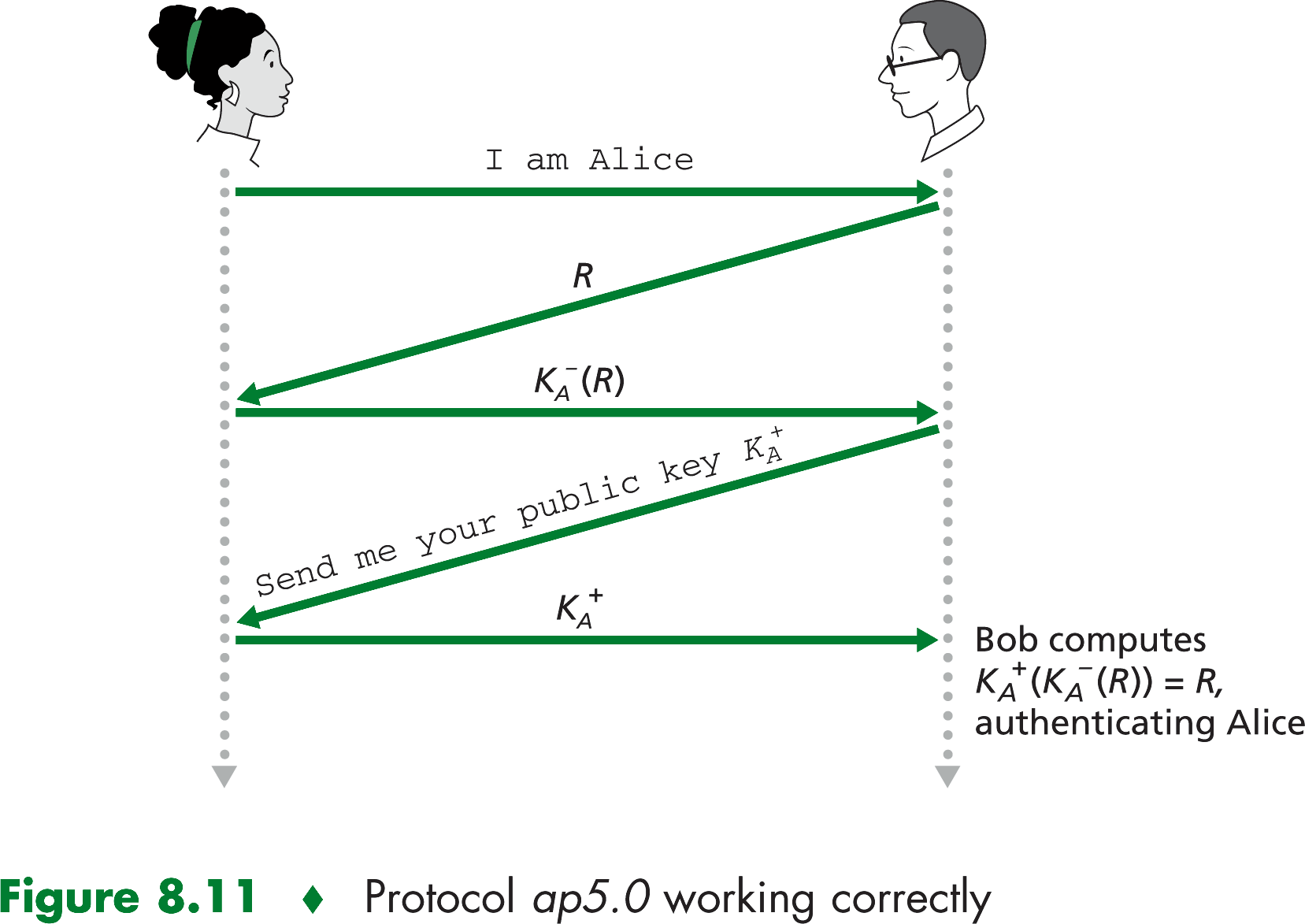
From this scenario it is clear that protocol ap5.0 is only as secure as the distribution of public keys. Fortunately,
there are secure ways of distributing public keys.
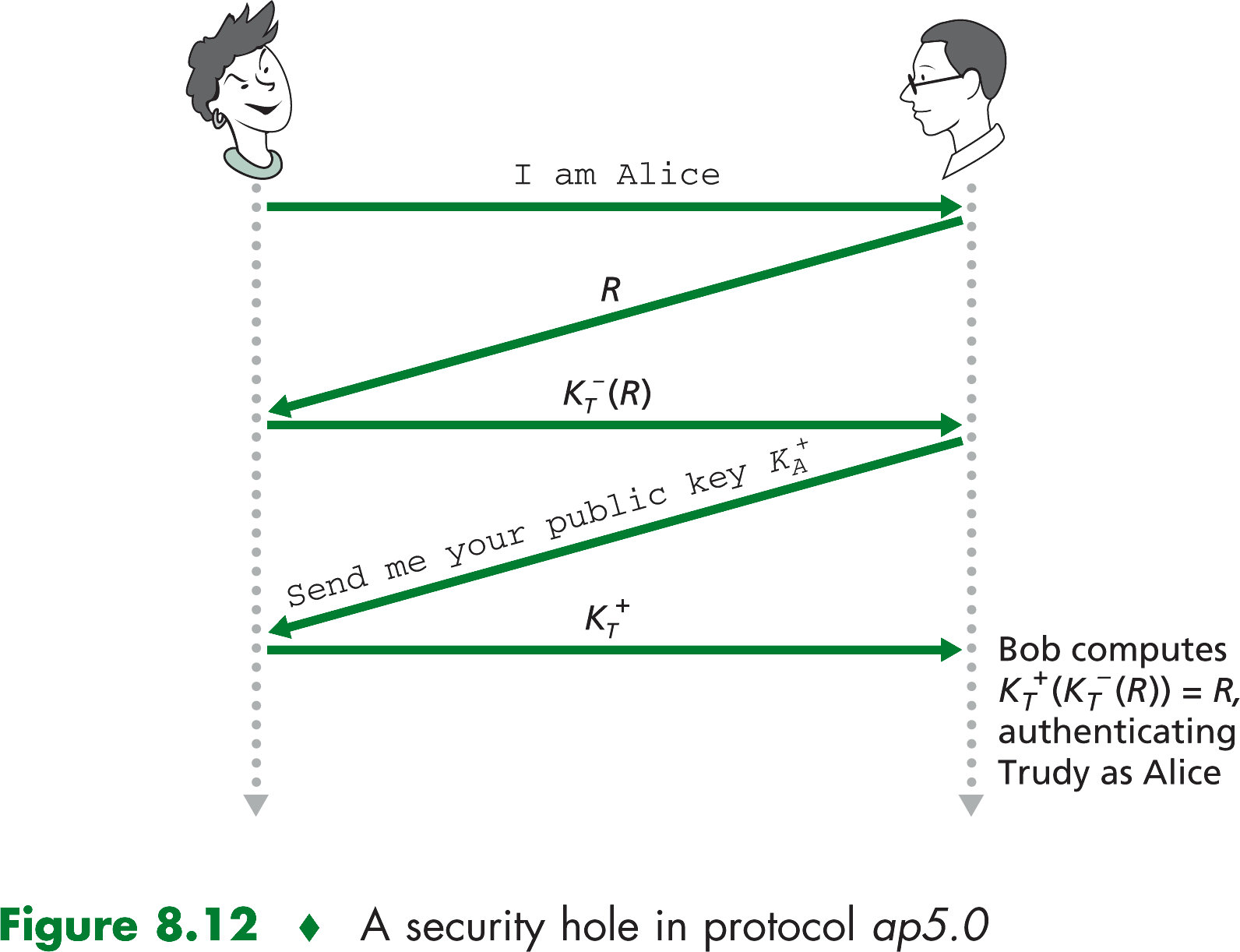
Eventually you might discover that something is amiss, your receiver will claim to have interacted with you, by you know
that you have never interacted with you receiver. There is an even more insidious attack that would avoid this detection.
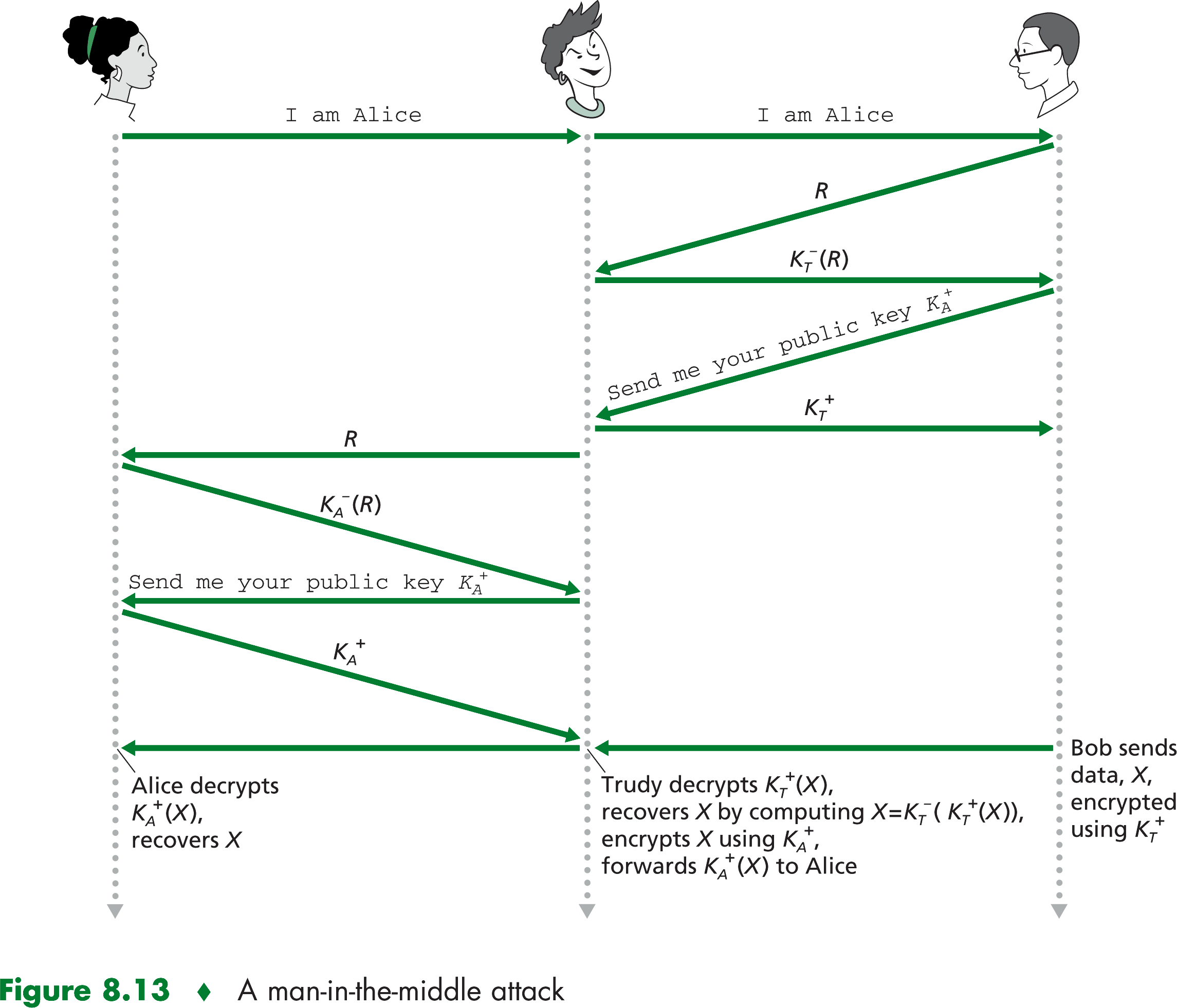
In the sceniro you are talking to your receiver, but by exploiting the same hole in the authentication protocol, someone is
able to transparently interpose themselves between you and your receiver. In particular, if your receiver begins
sending encrypted data to you using the encryption key they receiver from the other person. The other person can recover
the plaintext of the communication from you and your receiver.
|
