|
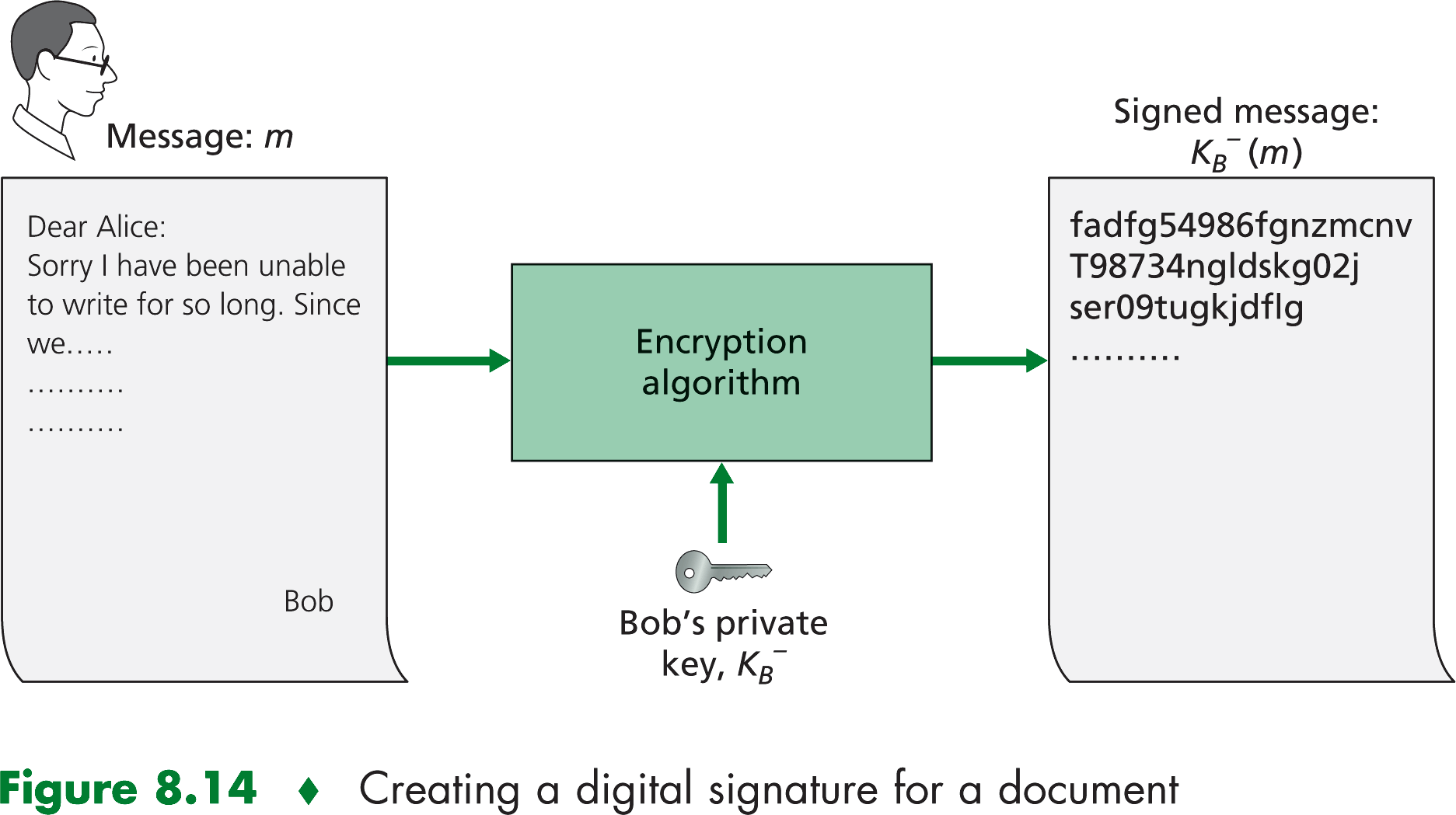
Suppose that you want to digitally sign a document, m. We can think of the document as a file or a message that
you are going to sign and send. to sign this document, you simply use your private key, k-B, to compute K-B(m).
It might seem odd that you are using your provate key to sign a document. Recall that encryption and decryption are
nothing more than a mathematical operation and recall that your goal is not to scramble or obscure the contents of the document,
but rather to sign the document in a manner that is verifiable, nonforgeable, and nonrepudible. You have the document,
m, and your digital signature of the document is K-B(m).
|
