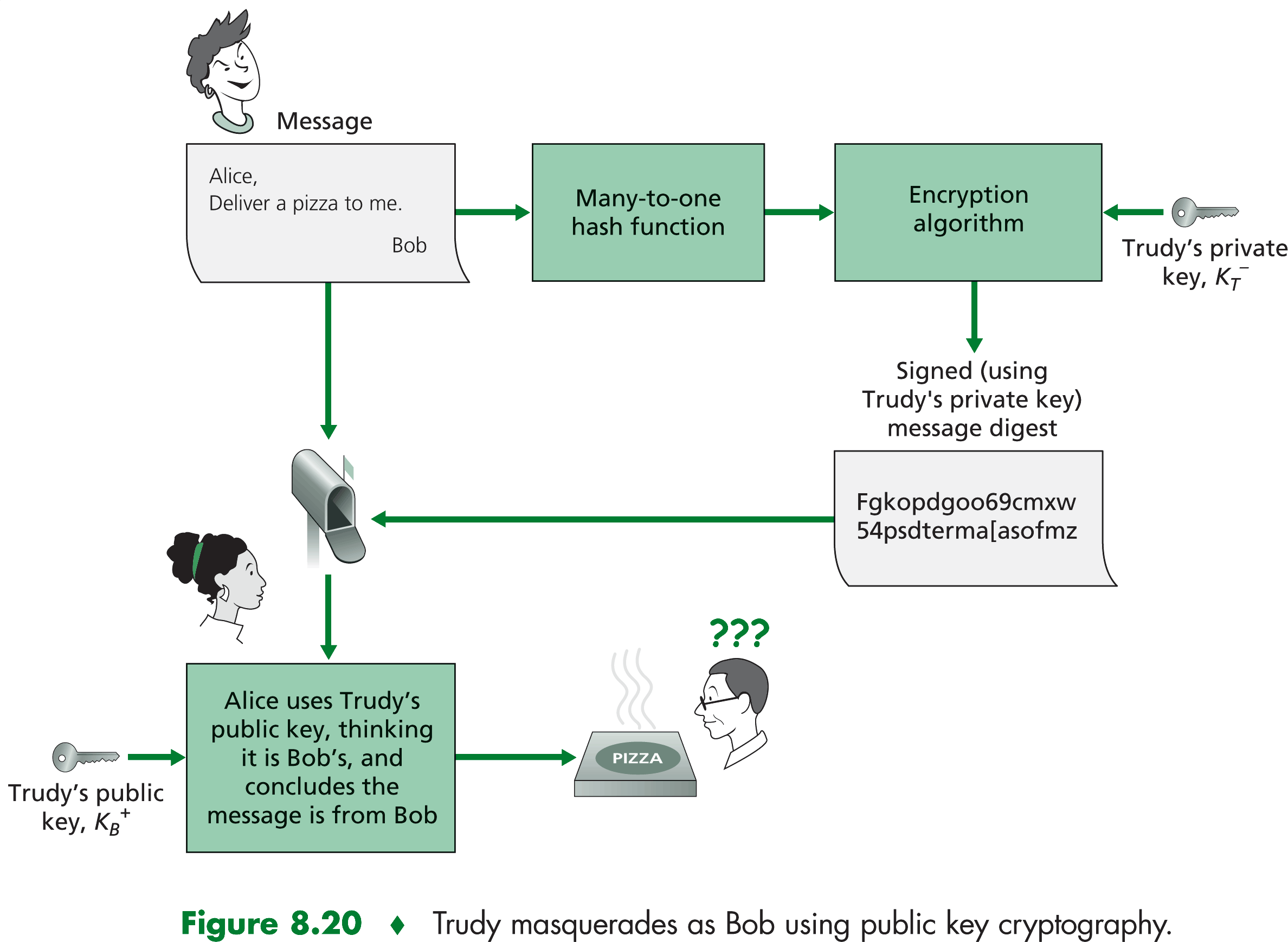
|
One of the principal features of public key cryptography is that it is possible for ftwo entities to exchange secret
messages without having to exchange secret keys.
With public key cryptograhpy, the communicating entities still have to exchange public keys. A user can make its
public key publicly available in many ways, for example, by posting the key on the user's personal Web page, by placing the
key in a public key server, or by sending the key to a correspondent by e-mail. A Web commerce site can plae its public
key on its server in a manner such that browsers automatically download the public key when connecting to the site.
Routers can place their public keys on public key servers, therby allowing other networks entities to retrieve them.
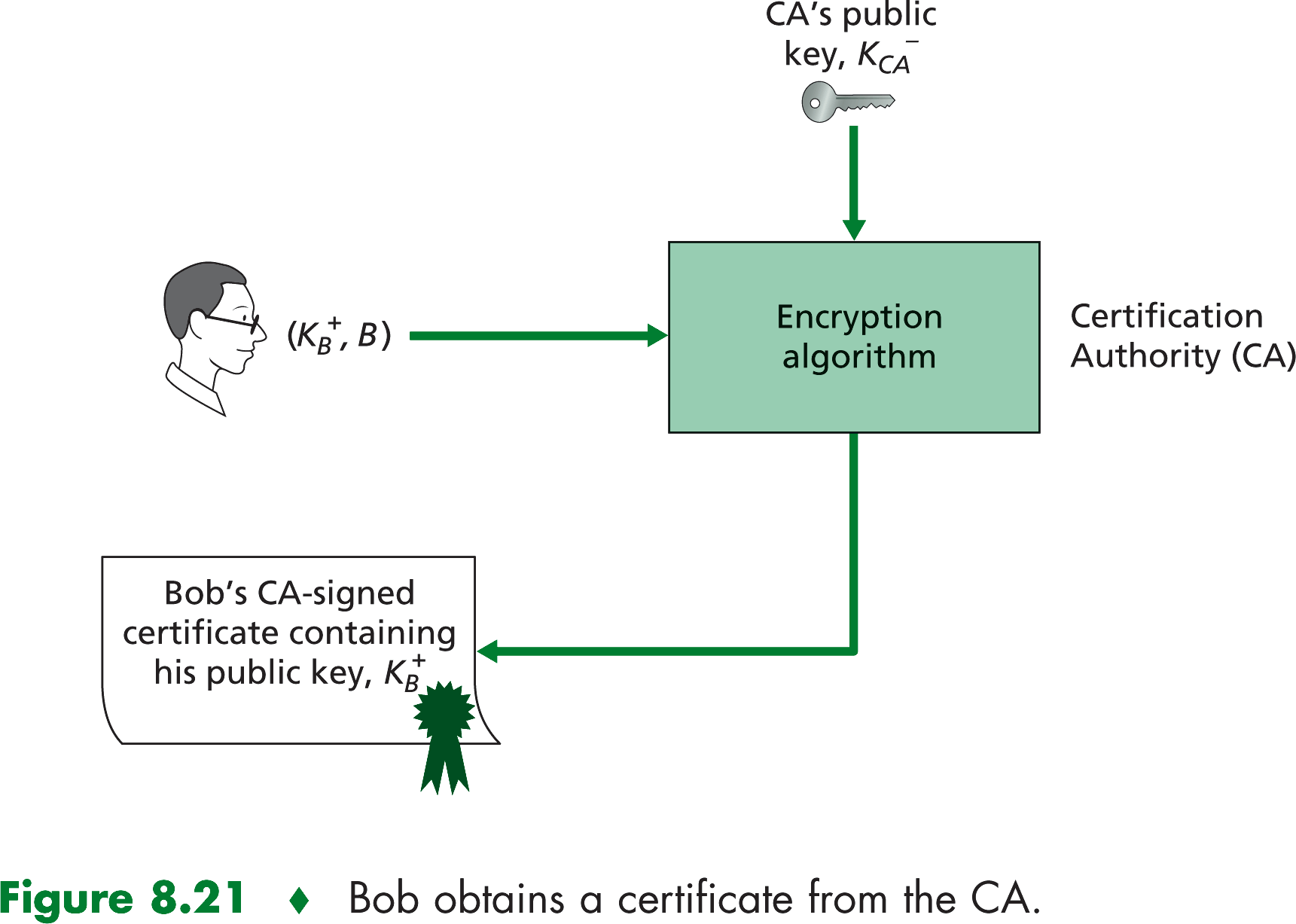
Binding a public key to a particular entity is typically done by a CA, whose job is to validate identities and issue
certificaties. A CS has the following roles.
- A CA verifies that an entity is who it says it is. There are no mandated procedures for how certification is done.
WHen dealing with a CA, one must trust the CA to have performetd a suitably rigorous identity verification.
- Once the CA verifies the identity of the entity, the CA creates a certificate that binds the public key
of the entity to the identity. The certificate contains the public key and globally unique identifying information about
the owner of the public key.
The International Telecommunication Union (ITU) and the IETF have developed standards for certificates. ITU X.509
[ITU 1993] specifies an authentication service as well as a specific syntax for certificates. [RFC 1422] describes CA-based
hey management for use with secure Internet e-mail. It is compatible with X.509 but beyond X.509 by establishing procedures
and convertions for a key management architecture.
With the recent boom in e-commerce and the consequent widespread need for secure transactions, there has been increased
interst in certificate authorities.
|
