|
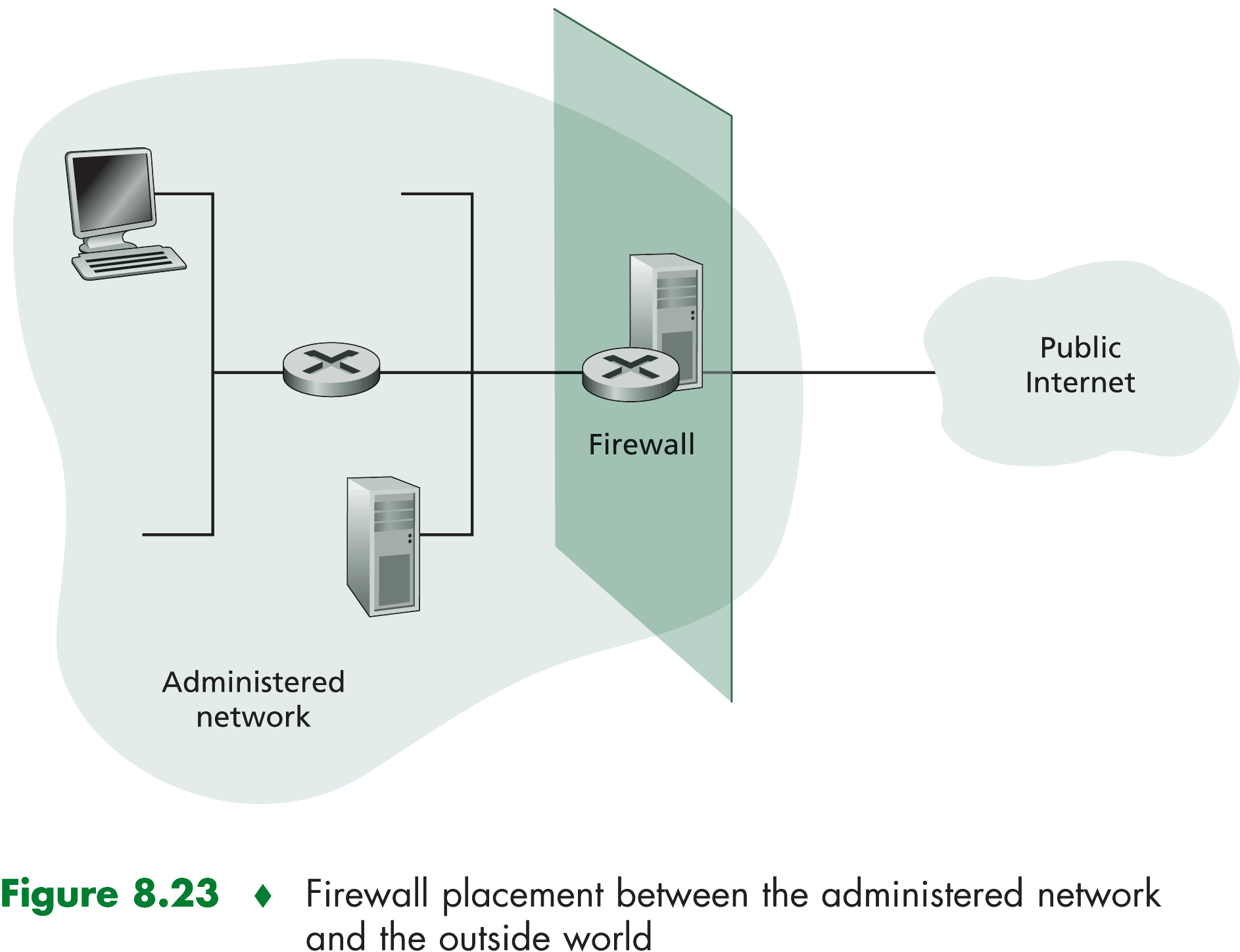
All traffic leaving and entering the internal network passes thorugh this router, and it is at this router where packet
filtering occurs. Packet filters operate by first parsing datagram headers and then applying filtering rulers
from an administrator-specified rule set to determine whether to drop the datagram or let the datagram pass. Filtering
decisions are typically based on
- IP source or destination address
- TCP or UDP source and destionation port
- ICMP message type
- Connection-intialization datagram using the TCP, SYN, or ACK bits
A filter can be set to block all UDP segments and all Telnet connections. Such a configuration prevents outsiders
from logging onto internal hosts using Telnet, and insiders from logging onto external hosts using Telnet commections, by
blocking all TCP segments whose source or destination port number is 232. Filtering UDP traffic is a popular policy
for corporations--much to the chargin of leasing audioand video-streaming vendors, whose products stream over UDP in the defalut
mode. Filtering Telnet connectionis is also popular, because it prevents outside a list of recommended port/protocol
packet filterings to avoid a number of well-known security holes in existing network applications.
A filtering policy can alos be based on the combination of addresses and port numbers. The filtering router can
forward all Telnet datagrams except those going to and coming from a list of specific IP addresses. This policy permits
Telnet commections to and from hosts on the allowed list. Unfortunately, basing the policy on external addressed provides
no protection against datagrams that have a source address belonging to a host on the allowed list but that in fact have been
sent by another host.
Filtering can also be based on whether or not the TCP ACK bit is set. This trick is quite useful if an organization
wants to let its internal clients connect to external servers but to prevent external clients from connecting to internal
servers.
|
