|
Internal netwrok often have multiple application gateways, for ewxample, gateways for Telnet, HTTP, FTP, and e-mail.
An organization's mail server and Web cache are application gateways.
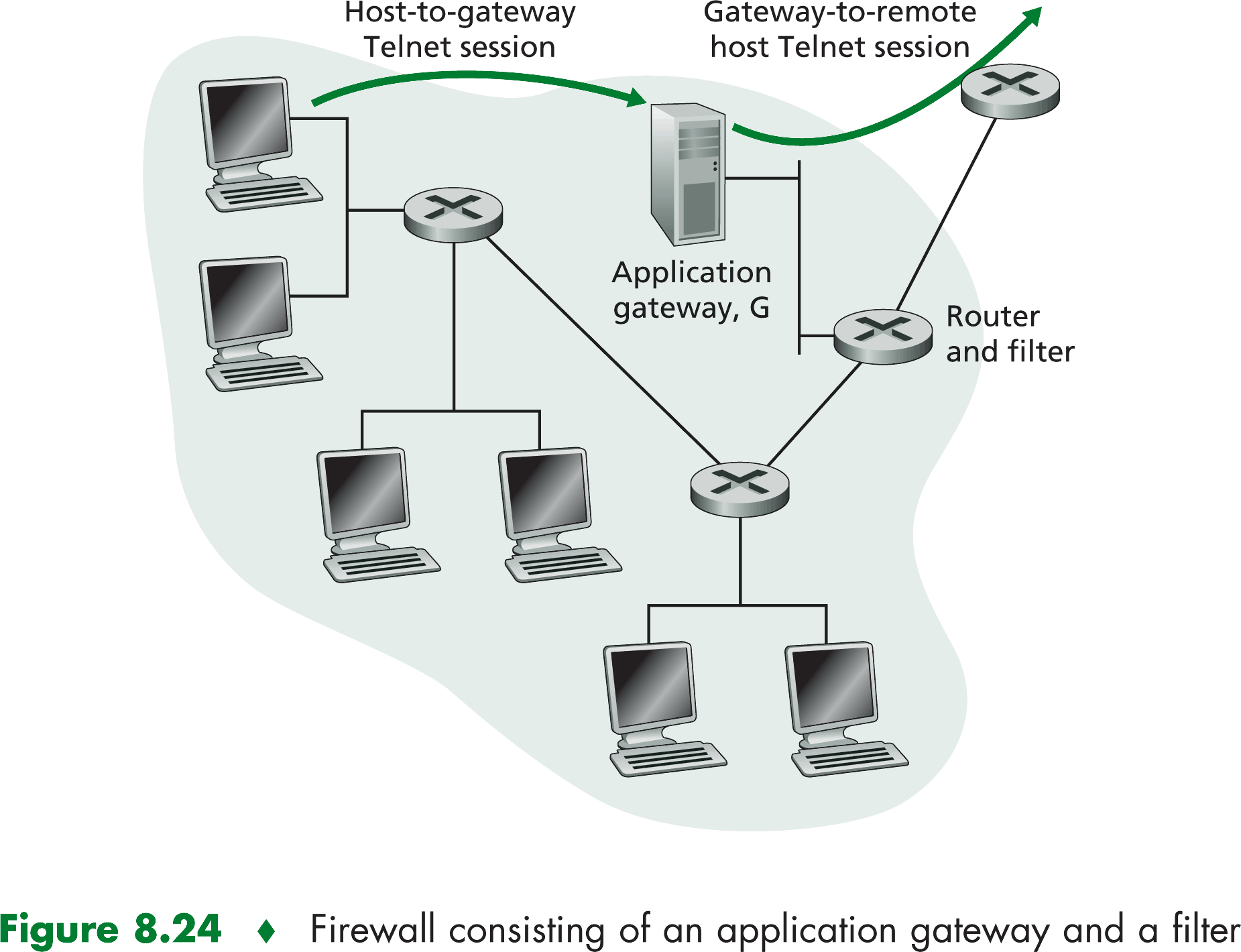
Application gateways do not cone without their disadvantages. First, a different application gateway is needed
for each application. Second, ther is a performance penalty to be paid, since all data will ve relayed via the gateway.
This becomes a concern particualarly when multiple users or applications are using the same gateway machine. Finally,
a certain amount of extra configuration effort must be taken; either
The client softarew must know how to contact the gateway instead of the external server when the user makes a request,
and must know how to tell the application gateway what external server to connect to, or
The user must explicitly connect to the external server through the application gateway.
Firewalls are by no means a panacea for all security problems. They introduce a tradeoff between the drgerr of
communication with the outside world and the level of security. Because filters can't stop spoofing of IP addresses
and port numbers, filters often use an all-or-nothing policy. Gateways can also have software bugs, allowing attackers
to penetrate them. Finally, firewalls are even less effective if internally generated communication can reach the outside
world without passing through the firewall. Wireless communication and dial-up modems are two such examples.
|
