|
The most strightforward way to provide confidentiality is for you to encrypt the message with symmetric key technology
and for your receiver to decrypt the message on receipt. If the symmetric key is long enough, and if only you and your
receiver have the key, then it is extremely difficult for straightforward, it has the fundamental difficulty. It is
hard to distribute a symmetric key so that only you and your receiver have copies of it. So we naturally consider an
alternative approach--public ke, and you send the encrypt message to your receiver's e-mail address. When your receiver
receives the message, they simply decrypt it with their public key, this approach is an excellent means to provide the desired
confidentiality.
PGP
Pretty Good Privacy (PGP) is an e-mail encryption scheme that has become a de facto standard.
Its Web site serves more than a million pages a month to users in 166 countries. Versions of PGP are available in the
public domain.
When PGP is installed, the software creates a public key pair for user. The public key can be posted on the user's
Web site or placed in a public key server. The private key is protected by the use of a password. The password
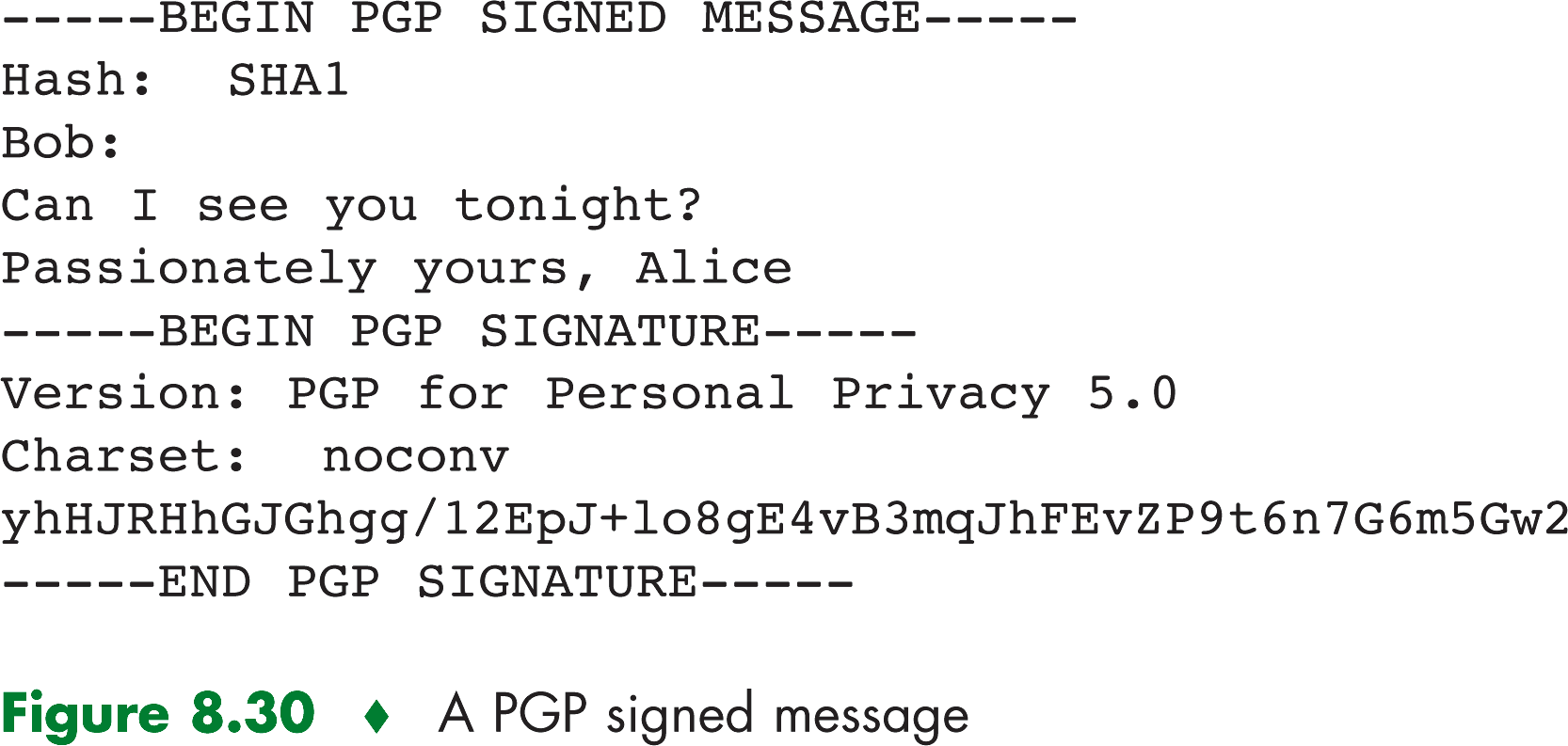
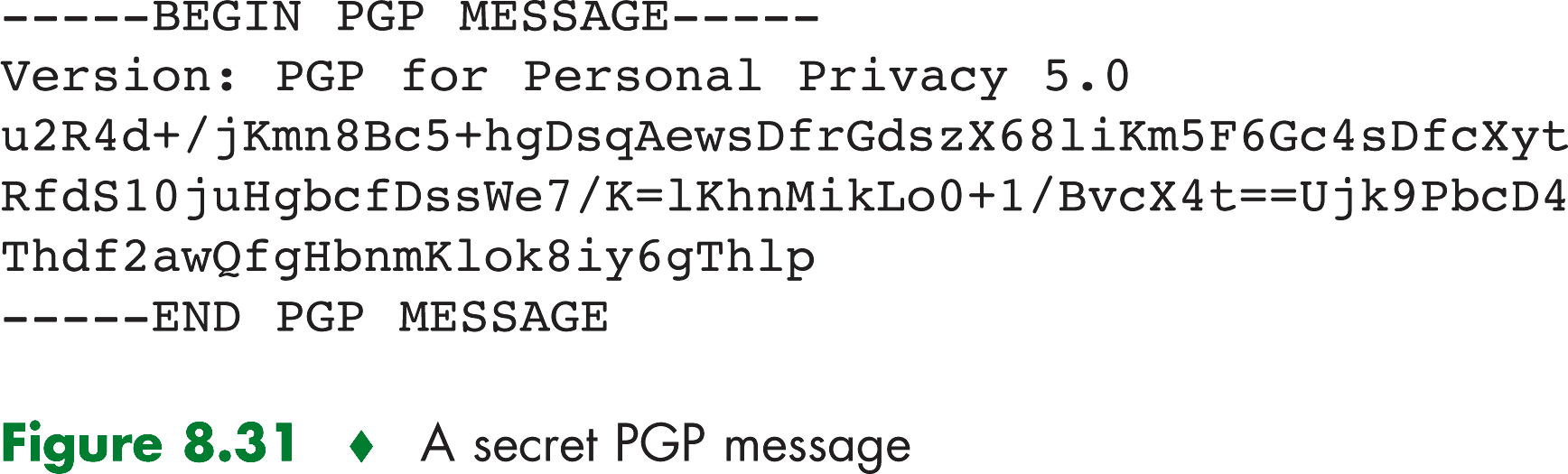
has to be entered every time the user accesses the private key. PGP gives the user the option of digitally signing the
message, encrypting the message, or both digitally signing and encrypting.
PGP also provides a mechanism for public key certification, but the mechanism is quite different from the more conventional
certificate authority. PGP public keys are certified by a web of trust. PGP public keys are also distributed by
PGP public key servers on the Internet. When a user submits a public key to such a server, the server stores a copy
of the key, sends a copy of the key to all the other public key servers, and sends the key to anyone who requests it.
Although key-signing parties and PGP public key servers actually exist, by far the most common ways for users to distribute
their public keys are by posting them on their personal Web pages and by advertising them in thier e-mails.
|
