|
Secure sockets layer (SSL), originally developed by Netscape, is a protocol designed to provide data
encryption and authentication between a Web client and a Web server. The protocol begins with a handshake phase that
negotiates an encryption algorithm and keys, and authenticates the server to the client. Optionally, the client can
also be authenticated to the server. Once the handshake is complete and the transmission of application data begins,
all data is encrypted using session keys megotiated during the handshake phase. SSL is widely used in Internet commerce, being
implemented in almost all popular browsers and Web servers.
SSL and TLS are not limited to the Web application, they can similarly be used for authentication and data encryption
for IMAP (Internet Mail Access Protocol) mail access. SSLcan be viewed as a layer that sits between the application
layer and the transport layer. On the sending side, SSL receives data, encrypts the data, and directs the encrypted
data to a TCP socket. On the receiving side, SSL reads from the TCP socket, decrypts the data, and directs the data
to the application. SSL can be used with many Internet applications, this is context of the Web for Internet commerce.
- SSL server authentication, allowing a user to confirm a server's identity.
- SSL client authentication, allowing a server to confirm a user's identity.
- An encrypted SSL session, in which all information sent between browser and server is encrypted by the sending
software and decrypted by the receiving software.
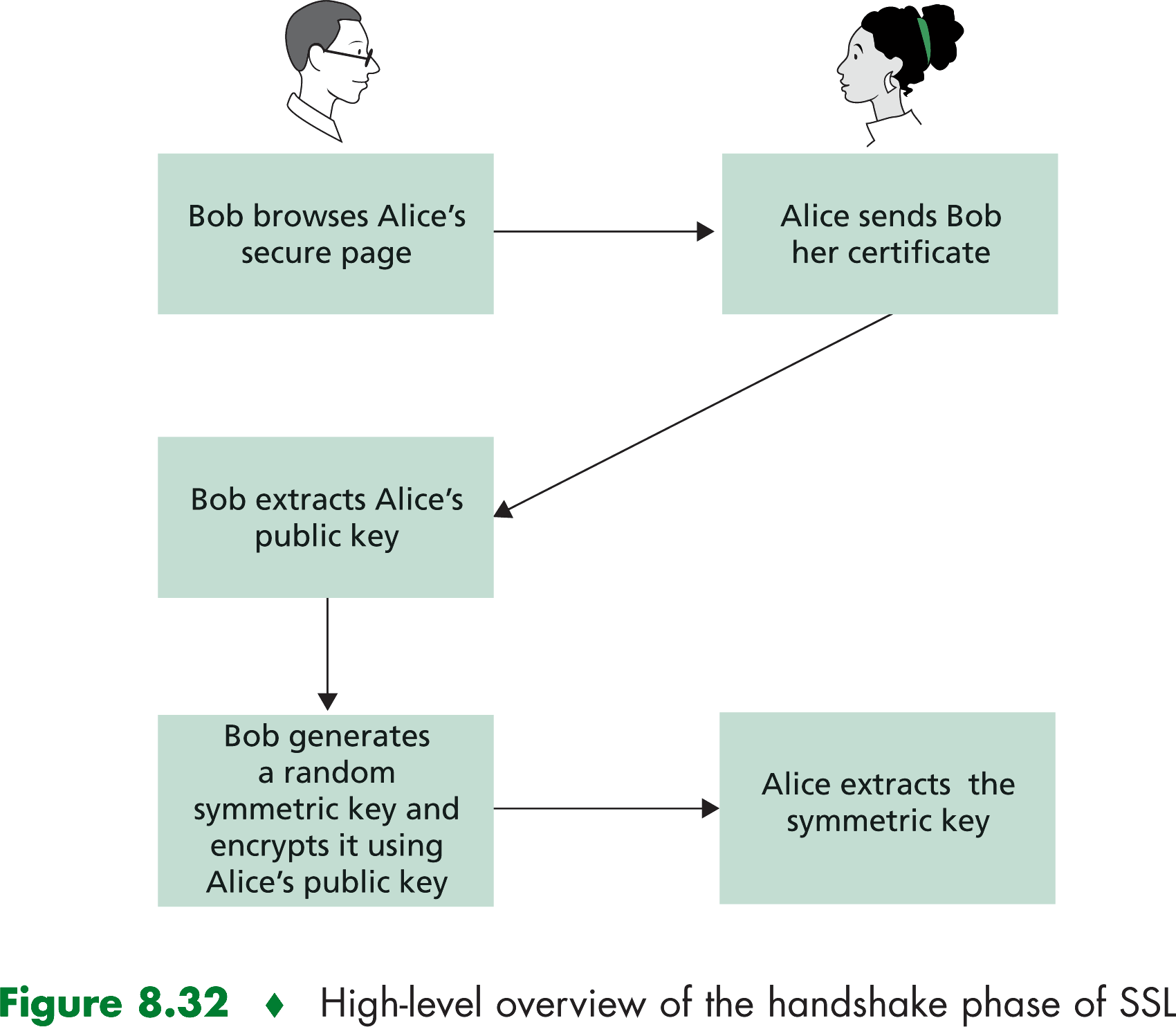
How SSL Works
- The browser sends the server the browsre's SSL version number and cryptographic preferences.
- The sercer sends the browser the server's SSL version number, cryptographic preferences, and its certificate.
- Thebrowser has a list of trusted CSa and a public key for each CA on the list.
- The browser generates a symmetric session key, encrypts it with the server's public key, and sends the encrypted session
key to the server.
- The browser sends a messafe to the server informing it that future messages from the client will be encrypted with the
session key.
- The server sends a message to the browser informing it that future messages from the server will be encrypted with the
session key.
- The SSL handshake is now complete, and the SSL session has begun.
|
